Best Network Security Solutions Dubai, UAE
In this modern era, cyber threats are increasing daily. Protecting data is important for companies, no matter what their size. Organizations face evolving threats and risks from malicious attacks and unauthorized access to software and hardware.
To tackle these problems, most companies in Dubai, UAE, are moving towards reliable network security solutions. In network security solutions, businesses use different techniques and tools to identify, reduce, and respond quickly to malicious cyber attacks.
In the face of these threats, organizations should take strict measures regarding the security and safety of their data. They should develop a robust network security system that protects files and personal data from unauthorized access and malicious attacks.
Network security solutions in Dubai, UAE, are essential as many companies share and store data daily. So, these solutions are important in protecting from hackers, cyber threats, and potential breaches.
Benefits of Network Security Solutions
The key advantages of installing network security solutions are numerous. Businesses in the UAE are moving towards advanced network security solutions. Here are some of the benefits of network security solutions.
- It helps to protect personal data from unauthorized access and potential breaches.
- These solutions secure information when shared between computers on the network.
- Controls all the information and provides authorized access to specific computers on the web.
- It guards the network against cyber-attacks and hackers from the internet.
Different Types of Network Security Solutions
When it comes to protecting your company’s network from cyber threats, you need multiple network solutions to secure your business network from attacks such as spyware, ransomware, hackers, and other threats.
Several organizations in all states of UAE including Abu Dhabi, Dubai, Sharjah, and Ajman are implementing different network security solutions to secure their valuable data and organization interests. Let’s explore different network security solutions to safeguard your network.
How Firewalls Fortify Your Network Against Threats?
The firewall works as a defender for your computer network. The main job of the firewall is to control and monitor all the traffic coming in and going out from the web. This way, a firewall fortifies your network from unauthorized breaches and bad stuff.
A firewall is available in both hardware and software forms and functions as the primary barrier for your network. Nowadays in Dubai, many organizations also go for alternative cloud-based firewalls hosted on remote servers.
Network security administrators can use and control the firewalls using a digital interface. A cloud-based firewall gives certain privileges to the user, like setting up the firewall and allowing and blocking certain types of traffic. The best firewalls you can get for network security solutions are Fortigate, Cisco, and WatchGuard.
Fortigate Firewall:

Fortigate firewall is commonly used in organizations to add more defense and protection from dangerous cyber attacks. They act as digital guards to secure the network from different cyber threats like malware, viruses, and ransomware.
Fortigate firewall offers advanced features such as deep packet inspection, stateful inspection, and VPN support. All these features act as superheroes to protect the network from bad stuff and unauthorized access.
Cisco Firewall:

Cisco Firewall is a security tool developed and designed by Cisco Systems. The main responsibilities of a Cisco firewall are the same as other firewalls; the difference comes in its techniques.
Cisco utilizes modern techniques like packet filtering, which thoroughly checks every data packet to determine if it should be entered based on the rules. Other features of the Cisco firewall are stateful inspection, intrusion prevention systems, and VPN capabilities. It combines all these features to secure the network from incoming and outgoing traffic.
Intrusion Detection System (IDS)
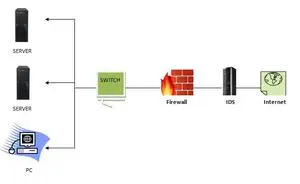
An intrusion Detection System is a security tool whose purpose is to determine and alert on any questionable or hostile activity in the network. The security operation center analysts respond to these alerts and threats by taking necessary actions.
Intrusion Detection System is effective, but sometimes it produces false alerts, requiring refining during installation. The proper installation of IDS involves defining normal network traffic to prevent unnecessary alarms. A Plethora of network security solution provider companies in Dubai, UAE are offering both IPS and IDS.
To ensure non-malicious traffic doesn’t enter the network, IDS uses SPAN or TAP ports to analyze copies of network packets. There are various IDS systems available in the market. Some of them are:
- Snort
- Suricata
- Zeek
- OSSEC
Intrusion Prevention System (IPS)
The intrusion prevention system has the same functions as IDS; its job is to stop any suspicious or malicious activity on the network. Unlike IDS, which only finds threats without taking action, the intrusion prevention system takes further steps by blocking, dropping, or reporting malicious activity.
IPS uses various techniques to identify threats, and it is positioned behind the firewall and in line with network traffic. The methods that it uses are:
- Signature-Based: Thoroughly matches all network activities with known threat signatures but is limited to realizing previously identified attacks.
- Policy-Based: Another great technique that IPS uses is to implement all the organization’s security policies; based on these policies, IPS blocks the violating activities.
- Anomaly-Based: Observe strange behavior by matching network activities to the baseline standard. More advanced IPS uses artificial intelligence and machine learning to enhance anomaly detection.
After finding any malicious activity, IPS can automate actions like alerting administrators, dropping packets, blocking traffic from the source, or resetting connections. IPS systems have a lot of key benefits, such as customization, compliance, time-saving, increased efficiency, and additional security. These days, great IPS systems are available, such as Trend Micro, FireEye, McAfee, and Secureworks.
Data Loss Prevention (DLP)
Data loss prevention uses the technique of locating and preventing the loss, leakage, and misuse of data that passes through breaches, ex-filtration transmissions, and unauthorized access. Many data loss prevention systems are available in Sharjah, UAE for network security solutions such as Forcepoint, Trellix, and Symantec.
DLP provides many key advantages to the organization regarding the network’s security. The benefits of using data loss prevention are
- It secures the applications’ data using user authentication and access control.
- It ensures that all the data transmitted over the network is secure.
- Furthermore, it uses access restrictions and user authentication to protect data stored at different network locations, including the cloud.
- Financial risk with data loss or leaks can also be reduced through DLP, especially in the case of ransomware attacks.
Business Continuity Plan (BCP)
The business continuity plan’s function is to protect personal assets and ensure quick recovery from potential threats like cyber attacks. A business continuity plan is essential to network security solutions because it allows organizations to be prepared in case of any troubles. The business continuity plan of companies should include the following:
- Addressing how risk influences the work
- Implementing different procedures and defense guards to mitigate risks.
- Test trials to ensure the procedure is effective
- Continuously checking and updating the plan.
Network monitoring
Network monitoring is an essential part of network security. It enables the optimal functioning of the computer network. In the context of network security solutions, effective monitoring safeguards against performance issues and plays a pivotal role in identifying and mitigating potential cybersecurity threats. This proactive approach is crucial in today’s complex corporate networks, especially with the widespread adoption of cloud and hybrid work environments.
Utilizing network monitoring and security solutions in Dubai offers numerous advantages. Some of them are listed below:
- Regular scanning helps see all connected devices in cloud networks, making it easier to spot and fix performance problems and security threats quickly.
- Automating monitoring tasks lightens the load on IT staff, allowing them to focus on important projects instead of routine duties.
- We avoid network downtime and keep business running smoothly by staying ahead with proactive monitoring. This efficient use of resources and staff focus also helps save costs.
Endpoint Security Solutions
Endpoint security is a vital approach to protect all the devices on the network from cyber threats. Companies use endpoint security solutions to protect the devices and prevent cyber criminals from exploiting the vulnerabilities and compromising sensitive data.
Endpoint security solutions are labeled as endpoint protection platforms, which include shields like firewalls, Next-generation Antivirus (NGAV), endpoint detection, and response systems. These shields work together to detect, analyze, and block attacks from the internet to ensure that devices connected to computer networks or cloud services are secure.
Ransomware attacks frequently target the computer systems on the network. Standard antiviruses may not stand against advanced ransomware, so the best solution is to use advanced endpoint detection and response solutions with Artificial intelligence. A grid can efficiently detect unknown malware and identify its behavior on endpoints through this method.
To sum it up, endpoint security is a fantastic solution for network security in the UAE. Using different strategies and AI capabilities, it protects against advanced and growing cyber threats, especially ransomware. You can get great endpoint security solutions from major vendors like Microsoft, McAfee, Sophos, and TrendMicro. All of these options are available in Dubai and other states of UAE.
Governance, Risk Management, and Compliance (GRC)
Many organizations in Dubai use a threefold strategy known as Governance, Risk Management, and Compliance to enhance network security and reduce all the risks the network can face in the future. Let’s discuss each of these strategies.
Governance: An organization creates and implements cybersecurity policies and procedures in this strategy. Furthermore, they also appoint a Chief Information Security Officer (CISO) and establish a risk management committee.
Risk Management: Developing and implementing risk management helps organizations focus on identifying, assessing, and prioritizing potential security risks and reducing them.
Compliance: Compliance means to implement all the relevant laws, regulations, and cybersecurity standards. Additionally, adherence to data privacy laws and industry-specific regulations.
GRC framework provides numerous benefits to organizations, including better compliance, increased operational efficiency, security posture, and improved collaboration. All gifts help to achieve a common goal of removing and protecting against cyber attacks.
Content Filtering Solutions
Content filtering solutions help the organization to filter and restrict access to objectionable content like emails, webpages, and executables. It is usually integrated into the internet firewalls, but you can also implement it in mail servers, routers, and DNS servers.
Content filtering identifies all the content that is not desirable by recognizing patterns in text strings or images. The objectionable content can be hate sites or illegal content. The only disadvantage of this security solution is that sometimes, it blocks legitimate content. You can get different options for content filtering solutions like WebTitan, Webroot, and CenturyLink.
Data Encryption and Protection
Data encryption and protection are essential to network security, which aims to secure all sensitive information from unapproved access. Encryption protects all types of data, for example, medical records and intellectual property, from theft and reduces legal and compliance issues.
The vital data, whether stored or at transmission, should always be encrypted. It can be achieved through both software and hardware controls. For example, through Secure Sockets Layer (SSL), you can put encryption on online transactions involving credit and debit cards. To further enhance the protection, encryption on hard drives of laptops and desktops is essential.
Security Information and Event Management (SIEM)
Security information and event management (SIEM) is a protection method that combines information and event management. It collects data and information from various sources, detects variations, and triggers action when hazardous issues arise. Now, many smaller organizations adopt SIEM due to concerns about advanced threats.
Initially, it was driven by Payment Card Industry Data Security Standard compliance. SIEM tools merge event and log data from systems like security devices, applications, and firewalls into a centralized platform. After that, it categorizes data into different categories like logins, malware activity, and potential threats. The top SIEM solution providers are SolarWinds and Splunk.
Why Pick Us
Alpha Capital Security Systems LLC is a renowned network security provider for organizations in Dubai. Our services cater to businesses of all sizes, ranging from small to large enterprises in Dubai and all over the UAE. Our primary objective is to address network security issues, provide reliable support, and help businesses grow. Our services offer a comprehensive security solution that safeguards your organization against new and existing security threats. We prioritize the development of new security services for emerging internet applications to ensure that your organization stays protected.
