IT Network Security Solution in Dubai
We Provide best IT Network Security Solution in UAE, Dubai, Abu Dhabi, Sharjah, Umm Al Qaiwain, Fujairah, Ajman and Ras Al Khaimah
IT Network Solution in Dubai
Alpha Capital Security Systems LLC is a reliable IT network security solution provider. We understand the importance of protecting your digital assets and confidential information in today’s connected world.
We provide complete network security services that enable your company to operate safely in the digital environment thanks to our cutting-edge technology and knowledge.
At Alpha Capital Security Systems LLC, we take pleasure in always being one step ahead of the constantly changing world of cyber threats.
In order to strengthen your network infrastructure, our team of qualified specialists will deploy strong security measures, uncover weaknesses, and prevent assaults.
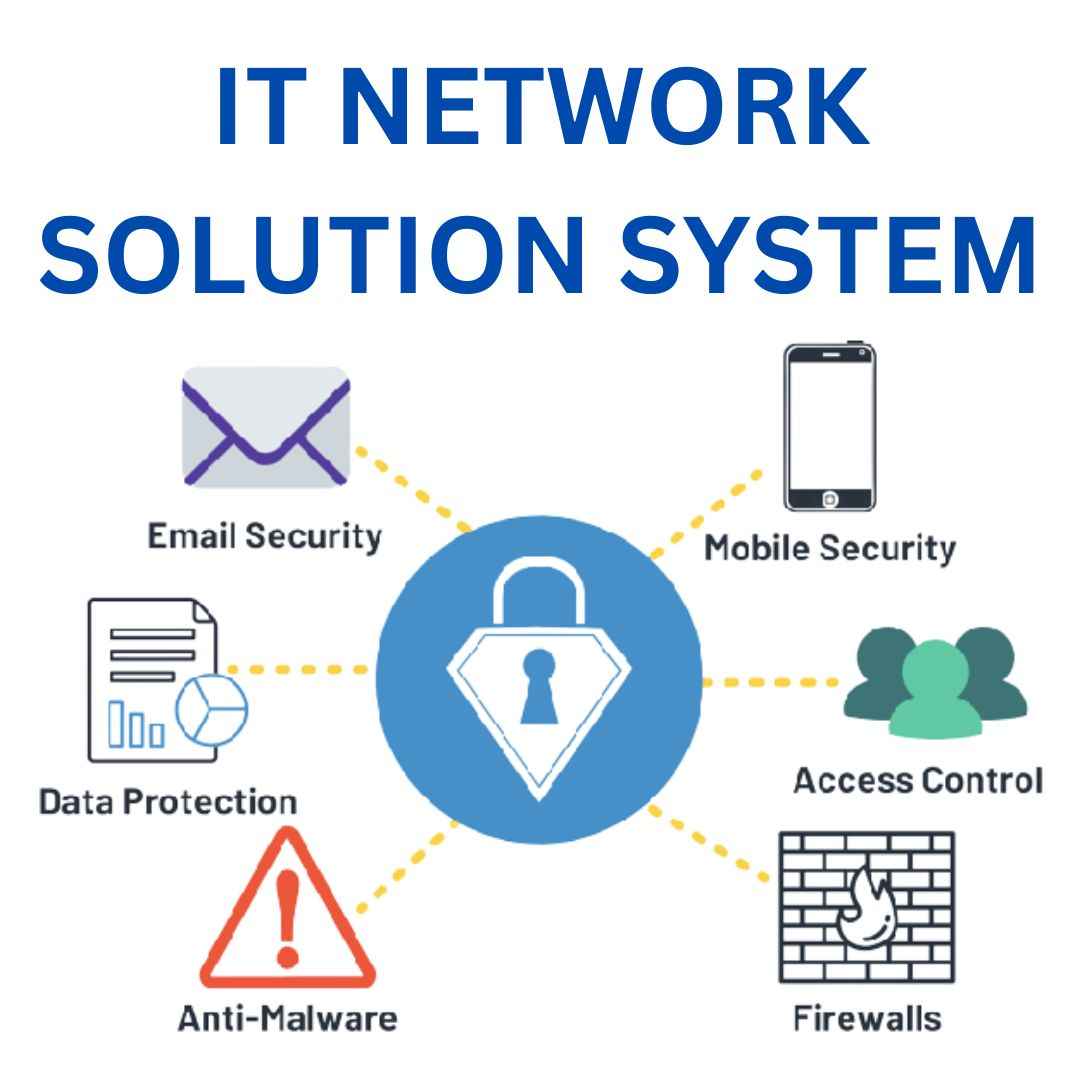
Table Of Content
Best IT Network Security Solution Provider in Dubai
In today’s digital world, cyber threats are a constant concern for businesses of all sizes. With the increasing sophistication of cyberattacks, it is more important than ever for businesses to have a robust IT network security solution in place.
Alpha Capital Security Systems LLC is a leading provider of IT network security solutions in Dubai. We offer a comprehensive suite of solutions and services to help businesses protect their networks from a wide range of cyber threats.
Our solutions include:
- Firewalls Solutions
- Structured Cabling
- Fiber Splicing
- Cloud Solutions in Dubai
- Network Attached Storage (NAS)
- Network Protocols Solutions
Intrusion detection systems
- Endpoint security
- Vulnerability management
- Security awareness training
- Security incident response
- Compliance assessment and support
We also provide a wide range of networking solutions, including:
- Network design and implementation: We can design and implement a network that meets the specific needs of your business, taking into account your budget, performance requirements, and security needs.
- Network management: We offer a range of network management services, including monitoring, maintenance, and troubleshooting.
- Network security: We can provide a variety of network security solutions, including firewalls, intrusion detection systems, and VPNs.
- Wireless networking: We can design and implement a wireless network for your business, providing your employees with secure access to the internet and other resources.
- Cloud networking: We can help you to migrate your network to the cloud, or to connect your on-premises network to the cloud.
Need A Free Consultant
Alpha Capital Security Systems LLC offers a free consultant service to help you identify and address your security concerns. Contact us today to schedule your consultation and protect what matters most.
The Importance of Network Security
Network security is essential for protecting sensitive data, ensuring business continuity, and fostering trust.
- Sensitive data protection: Network security keeps personal data, financial records, and intellectual property safe from unauthorized access, theft, or misuse.
- Business continuity: Network security prevents cyberattacks from disrupting business operations and causing financial losses and productivity declines.
- Reputation management: Network security demonstrates to users, clients, and partners that the organization is committed to protecting their data and privacy. This helps to build trust and enhance the organization’s reputation.
Firewall Solutions in Dubai
Firewalls are essential security devices that protect networks from unauthorized access and malicious traffic. They work by inspecting and filtering all incoming and outgoing data packets based on a set of pre-defined rules. This helps to keep sensitive data safe, prevent disruptions to business operations, and build trust with users, clients, and partners. Alpha Capital Security Systems LLC Provide you all types of firewall solution in Dubai, UAE.
Web Application Firewall
A Web Application Firewall (WAF) is a specialized security solution that protects web applications from a variety of online threats and attacks. It works by inspecting all incoming and outgoing web traffic and filtering out malicious or suspicious activity.
WAFs are essential for businesses of all sizes, as web applications are a primary target for cyberattacks. WAFs can help to protect sensitive data, maintain regulatory compliance, and ensure the availability and reliability of online services.
Here are some of the key benefits of using a WAF:
- Protection against common web attacks: WAFs can protect against a wide range of common web attacks, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
- Improved security posture: WAFs can help organizations to improve their overall security posture by providing features such as rate limiting, content filtering, and access control policies.
- Visibility and insights: WAFs provide valuable insights into web traffic and attack attempts, which can help security teams to proactively address vulnerabilities and emerging threats.
Overall, a WAF is an essential security component for any organization that relies on web applications.
Next Generation Firewall
Next-Generation Firewalls (NGFWs) are advanced cybersecurity solutions that go beyond the capabilities of traditional firewalls to protect against complex and evolving cyber threats.
NGFWs offer a number of key advantages over traditional firewalls, including:
- Deep packet inspection: NGFWs can inspect the contents of data packets at a granular level, enabling them to identify and block threats that traditional firewalls may miss.
- Intrusion prevention: NGFWs can proactively prevent known and unknown attacks by inspecting traffic for suspicious patterns and anomalies.
- Application-awareness: NGFWs can identify and understand applications running on the network, allowing them to apply security policies based on the risk associated with each application.
- SSL/TLS decryption: NGFWs can decrypt encrypted traffic to inspect it for threats, even if it is using the latest encryption standards.
- Integration with other security solutions: NGFWs can be integrated with other security solutions, such as intrusion detection systems and security information and event management (SIEM) systems, to provide a comprehensive and coordinated approach to network security.
NGFWs are an essential component of a comprehensive cybersecurity strategy for organizations of all sizes. They offer advanced protection against a wide range of cyber threats, including malware, ransomware, and zero-day vulnerabilities.
Common Network Security Threats
Malware Attacks
Malicious software, or malware, is a ubiquitous threat in the digital realm. It includes viruses, worms, Trojans, ransomware, and spyware, among others. These programs are designed to infiltrate systems, steal data, disrupt operations, or demand ransoms. IT Network Security Solution plays a pivotal role in defending against malware attacks, ensuring the safety of digital assets.
Phishing and Social Engineering
Phishing attacks involve tricking individuals into revealing sensitive information, such as login credentials or financial details. Social engineering techniques manipulate human psychology to gain unauthorized access. An effective IT Network Security Solution is essential to thwart phishing attempts and protect against social engineering tactics.
DDoS Attacks
Distributed Denial of Service (DDoS) attacks flood a network or website with an overwhelming volume of traffic, rendering it unavailable to users. Implementing a robust IT Network Security Solution is crucial to mitigate the impact of DDoS attacks and maintain network accessibility.
Insider Threats
Insider threats originate from within an organization. They can be employees, contractors, or business associates with access to sensitive data and systems, who intentionally or unintentionally compromise security. IT Network Security Solution helps organizations detect and address insider threats, safeguarding their digital infrastructure.
IT Network Security Solution serves as a comprehensive defense mechanism against a wide range of threats, including malware attacks, phishing, DDoS attacks, and insider threats. It ensures the integrity and security of digital assets in today’s complex digital landscape. IT Network Security Solution is your shield against evolving cyber threats.
The Components of Network Security
Firewalls and Intrusion Detection Systems (IDS)
Firewalls act as barriers between a trusted network and untrusted external networks. Intrusion Detection Systems monitor network traffic for signs of malicious activity. Implementing an IT Network Security Solution is essential to effectively manage firewalls and IDS, safeguarding your digital infrastructure.
Antivirus and Anti-Malware Software
Antivirus and anti-malware software scan files and programs for known threats and remove or quarantine them. IT Network Security Solution includes robust antivirus and anti-malware components to shield your systems from malware threats.
Secure Access Control
Access control mechanisms determine who can access what information and resources within a network. IT Network Security Solution incorporates secure access control protocols to ensure that only authorized individuals can access sensitive data.
Encryption
Encryption transforms data into a code to prevent unauthorized access during transmission or storage. IT Network Security Solution employs encryption techniques to protect data confidentiality and integrity.
Types of IT Network Security Protections
- Firewall. Firewalls control incoming and outgoing traffic on networks, with predetermined security rules. …
- Network Segmentation. …
- Remote Access VPN. …
- Email Security. …
- Data Loss Prevention (DLP) …
- Intrusion Prevention Systems (IPS) …
- Sandboxing. …
- Hyperscale Network Security Solution.
Network Segmentation in Dubai
Network Segmentation is a fundamental IT Network Security Solution that involves dividing a computer network into smaller, isolated segments or subnetworks. This strategy enhances security by limiting access between segments, reducing the attack surface, and containing potential security breaches.
IT Network Security Solution Network Segmentation helps organizations safeguard their critical assets and data from unauthorized access, malware, and other threats.
By logically separating different parts of a network, IT Network Security Solution Network Segmentation ensures that sensitive information remains protected within designated segments, and potential attackers are prevented from moving laterally through the network.
IT Network Security Solution Network Segmentation enables organizations to implement more stringent security policies and controls within each segment. It allows for the customization of security measures based on the specific needs and risks associated with different network areas
Remote Access VPN in Dubai
A remote access VPN is like a secure tunnel that connects a remote user’s device to a corporate network. This tunnel encrypts all data that is transmitted through it, making it unreadable to anyone who tries to intercept it.
Remote access VPNs are essential for businesses that have employees who work remotely, as they allow those employees to access the company’s network and resources without sacrificing security.
Here are some of the key benefits of using a remote access VPN:
- Security: Remote access VPNs encrypt all data that is transmitted through them, making it unreadable to anyone who tries to intercept it. This helps to protect sensitive data, such as customer records and financial information, from unauthorized access.
- Convenience: Remote access VPNs allow employees to access the company’s network and resources from anywhere in the world, as long as they have an internet connection. This makes it possible for employees to work remotely, which can improve productivity and reduce costs.
- Compliance: Some industries, such as healthcare and finance, are required to comply with strict data security regulations. Remote access VPNs can help businesses to comply with these regulations by protecting sensitive data from unauthorized access.
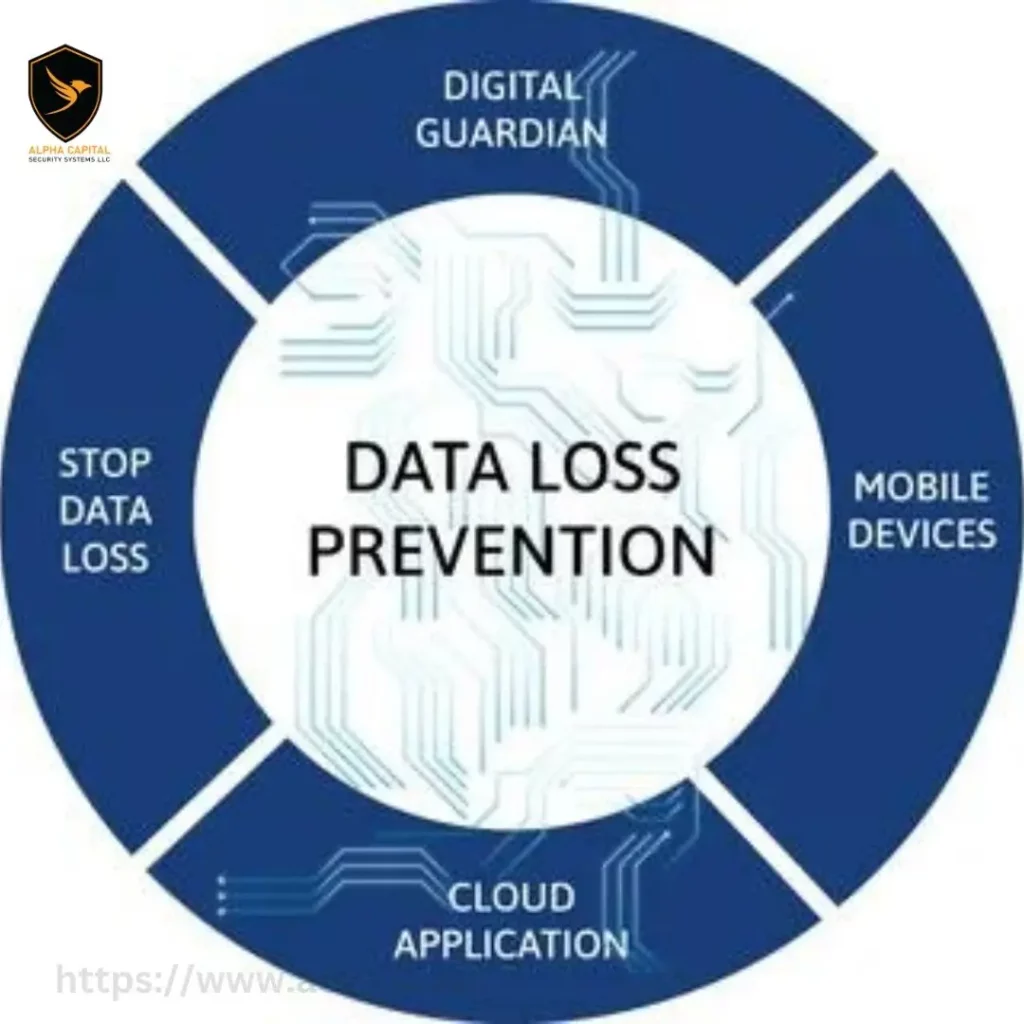
Data Loss Prevention (DLP) in Dubai
Data loss prevention (DLP) is a critical component of IT network security that aims to prevent the unauthorized disclosure or leakage of sensitive data. DLP solutions use a combination of technologies, policies, and procedures to identify, monitor, and protect sensitive information across networks, endpoints, and data storage systems.
DLP solutions can help to protect sensitive data from a variety of threats, including:
- Insider threats: Employees who accidentally or maliciously expose sensitive data.
- External threats: Hackers and other cybercriminals who attempt to steal sensitive data.
- Data breaches: Unauthorized access to sensitive data, such as through a ransomware attack or a lost laptop.
Intrusion Prevention Systems (IPS) in Dubai
Intrusion prevention systems (IPS) are essential security solutions that monitor network traffic in real time and block malicious activity and unauthorized access attempts. IPS solutions combine the capabilities of firewalls and intrusion detection systems (IDS) to provide comprehensive threat detection and prevention.
IPS work by inspecting all incoming and outgoing network traffic for known and unknown threats. If a threat is detected, the IPS can block the traffic, alert the security team, or take other actions to mitigate the risk.
IPS are an important part of any IT network security solution, as they can help to protect organizations from a wide range of threats, including:
- Malware
- Ransomware
- Denial-of-service attacks
- Data breaches
IPS can also help organizations comply with industry regulations that require them to protect their networks and data.

Benefits Of IT Network Security in Dubai
Protection against cyber threats:
A network’s architecture, data, and computer systems are all protected by network security against numerous cyber threats such as viruses, malware, hacking attempts, and unauthorized access. Organizations may lower their risk of cyberattacks and data breaches by putting strong security measures in place.
In order to protect networks, systems, and data from unauthorized access, attacks, and vulnerabilities, several techniques and technologies must be used as part of an IT network security solution.
Data confidentiality and integrity:
Access restrictions and other network security measures guarantee that private information sent over the network is kept private and cannot be intercepted or altered by unauthorized parties. Important data, such as client information, financial records, and intellectual property, may remain accurate and private thanks to this.
Implementing safeguards to prevent unauthorized access to or exposure of sensitive data is part of an IT network security solution data confidentiality strategy.
Improved productivity and availability:
A secure network reduces the likelihood of network outages and interruptions brought on by security events. Organizations may improve network dependability, guarantee ongoing resource availability, and allow staff to operate productively and uninterruptedly by putting in place safeguards like firewalls, intrusion detection systems, and load balancing.
FAQS
Q: What is IT Network Security Solution, and why is it important in Dubai?
IT Network Security Solution in Dubai refers to a comprehensive set of measures and technologies designed to protect digital infrastructure from cyber threats. It is crucial in Dubai due to the city’s increasing reliance on digital technologies for business and communication. With IT Network Security Solution, organizations in Dubai can ensure the security and confidentiality of their data.
Q: How can IT Network Security Solution benefit businesses operating in Dubai?
IT Network Security Solution offers multiple benefits to businesses in Dubai. It helps in safeguarding sensitive data, ensuring business continuity, maintaining customer trust, and complying with regulatory requirements. It also helps organizations respond effectively to the evolving threat landscape.
Q: What are the common cyber threats that IT Network Security Solution addresses in Dubai?
IT Network Security Solution in Dubai addresses various cyber threats, including malware attacks, phishing, DDoS attacks, and insider threats. It provides a multi-layered defense to mitigate these risks and protect digital assets.
Q: Are there specialized IT Network Security Solution providers in Dubai?
Yes, Dubai has a thriving IT industry with several specialized IT Network Security Solution providers. These companies offer tailored solutions to meet the unique security needs of businesses operating in the region.
Q: How can I choose the right IT Network Security Solution for my organization in Dubai?
Selecting the right IT Network Security Solution in Dubai involves assessing your organization’s specific requirements, considering scalability, compatibility, and cost-effectiveness, and consulting with reputable security experts. It’s essential to choose a solution that aligns with your business objectives and the unique challenges faced in the Dubai market.
