
Network Access Control System In Dubai
Dubai, like many other modern cities, has implemented Network Access Control System to enhance security and manage access to its networks. Network Access Control System systems are designed to ensure that only authorized devices and users can connect to a network, thereby protecting against unauthorized access, data breaches, and other cybersecurity threats. While I don’t have access to real-time information, I can provide a general overview of Network Access Control System systems and their implementation.
Network Access Control System Solutions
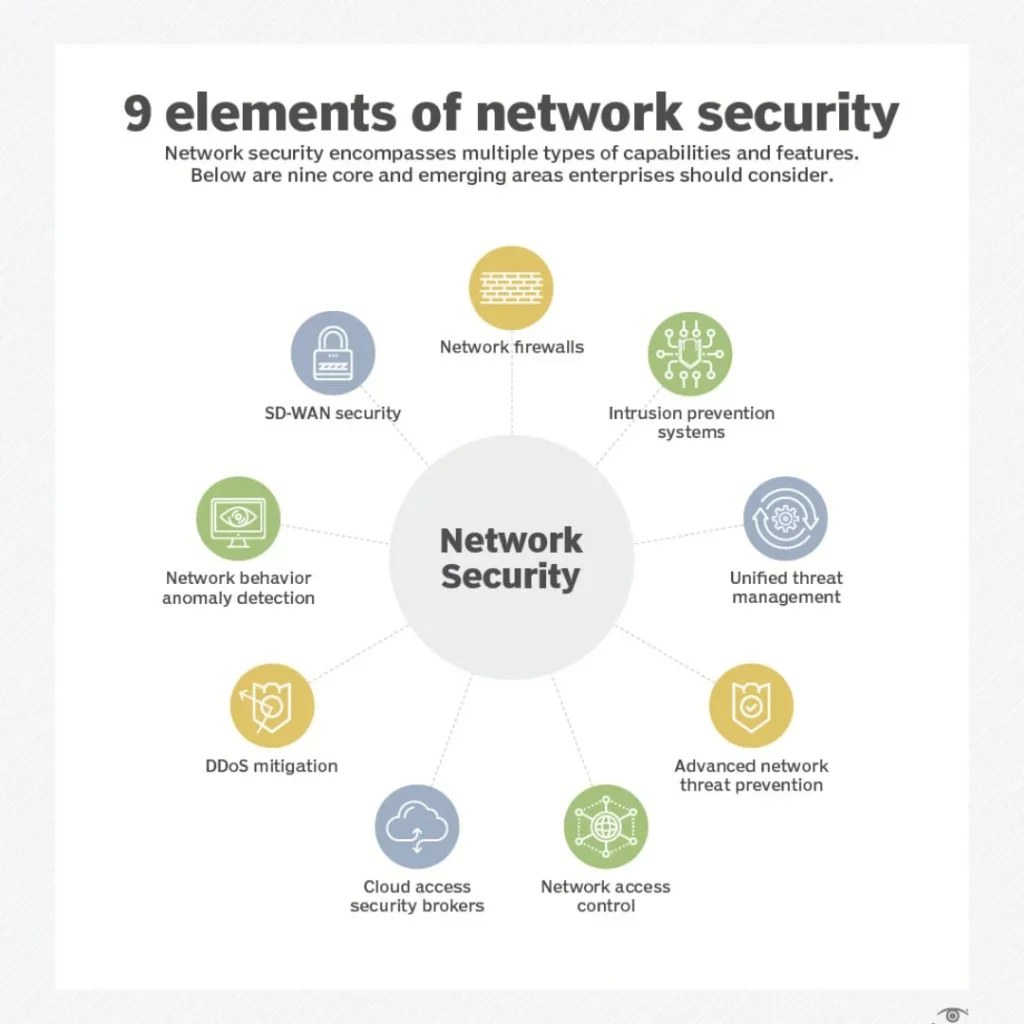
Network Access Control (NAC) systems provide security solutions for controlling and managing network access. These solutions authenticate and authorize devices before granting access, ensuring only authorized devices can connect to the network. Network Access Control System systems also enforce security policies, detect and remediate threats, and monitor network activity. They are crucial for maintaining network integrity and preventing unauthorized access or malicious activities.
Components And Features Commonly found in NAC Systems
Authentication
Network Access Control System often require users and devices to authenticate before they can connect to the network. This can be achieved through various methods such as username/password authentication, digital certificates, biometrics, or two-factor authentication.
Endpoint Compliance
Network Access Control System can assess the compliance of connecting devices with predefined security policies. This ensures that devices meet certain security standards, such as having up-to-date antivirus software, operating system patches, and other necessary security configurations.
Network Visibility
Network Access Control System provide administrators with real-time visibility into the devices and users connected to the network. This visibility enables better network management, troubleshooting, and identification of potential security threats.
Access Control
Once authenticated and assessed for compliance, Network Access Control System enforce access control policies based on user roles, device types, or other predefined criteria. These policies determine what resources or services a user or device can access within the network.
Remediation
In case a device does not meet the compliance requirements, Network Access Control System can initiate remediation actions, such as blocking network access, redirecting the device to a remediation server to resolve the issues, or quarantining the device until it meets the necessary security standards.
Importance Of Network Access Control System
Network Access Control Systems are crucial components of modern network security infrastructure. They play a vital role in protecting networks from unauthorized access, ensuring the integrity and confidentiality of sensitive information, and mitigating security risks. Here are some key reasons highlighting the importance of a Network Access Control system
Enhanced Security
Network Access Control System provide a strong security layer by enforcing authentication and authorization mechanisms. They verify the identity of users and devices attempting to connect to the network, ensuring that only authorized individuals and devices gain access. This helps prevent unauthorized access, malicious activities, and data breaches.
Endpoint Security
Network Access Control System monitor and assess the security posture of endpoints (such as laptops, smartphones, IoT devices) before granting them network access. They can enforce policies to ensure that endpoints meet security requirements, such as having updated antivirus software, patched operating systems, and compliant configurations. This helps protect the network from compromised or vulnerable devices that could be exploited by attackers.
Types of Access In NAC
In a Network Access Control System, access can be granted in a variety of ways. The most typical of these are:
- Device-Based Access: Security Devices get access in view of their identity and security status. A gadget in the NAC framework gets access to the organization, while a suspicious one might get restricted or have no entrance.
- User-Based Access: Access is granted to users based on their identity and role. Executives might have full organization access, while normal workers could have restricted admittance.
- Application-Based Access: Access is determined by the security requirements of the applications. High-risk applications could get restricted or no entrance, while generally safe ones appreciate full access.
- Location-Based Access: Where a gadget is located matters. Secure regions award full access, while unstable regions might restrict or deny access.
- Time-Based Access: Access changes rely upon the hour of the day. During business hours, full access might be given, yet outside business hours, access may be restricted or denied.
- Policy-Based Access: Specific policies or rules govern access. Gadgets that meet specific measures, such as having great security and being signed up for the NAC framework, may get full access.
- Guest-Based Access: It is a kind of access given to brief clients like guests, workers for hire, and merchants. Guest access can be granted in a number of different ways, including through specialized login portals, distinct guest networks, or VLANs.
How to Choose a Best NAC Solution:
Consider the following when selecting the appropriate Network Access Control System device in 2023:
- Network Size.
- Types of Devices.
- Features.
- Budget.
- Security.
- Usability.
- Vendor Support.
The right Network Access Control System device for your organization depends on what it needs and can afford.
Control over Access
Network Access Control System provide granular control over network access based on user roles, device types, locations, and other attributes. They can enforce different access policies for different groups of users or devices, ensuring that users have access only to the resources they need for their roles.
This helps limit the attack surface, reduce the risk of lateral movement by attackers, and prevent unauthorized access to sensitive data or critical systems.
Zero Trust Network Access
Zero Trust Network Access (ZTNA) is a security method that assumes that no user or device can be trusted completely, even when they are within the network’s protective boundary. Instead, ZTNA checks users’ and devices’ identities as well as their security status before allowing them onto the network.
Access is granted based on who or what the device is in a typical network access control (NAC) system. This approach expects that devices and clients inside the organization are protected. However, this trust is no longer valid in today’s world, where attackers can compromise network users and devices.
When a gadget or client is confirmed, they’re given admittance just to what they need to take care of their business. This protects sensitive data and reduces the likelihood of attacks.
ZTNA is an effective security strategy, but it is not a magic bullet. Other security measures, such as firewalls, intrusion detection systems, and data loss prevention systems, are essential.
Advantages of ZTNA:
- Better Security.
- Improved User Experience.
- Cost saving.
Challenges of ZTNA:
- Complexity.
- Cost.
- Dependency.
In conclusion, ZTNA is an effective security strategy that can assist in shielding networks from a variety of threats. Nonetheless, gauging its advantages and difficulties before involving it in your organization is fundamental
Conclusion
A Security Measure known as Network Access Control (NAC) controls who and what can enter a network. Before granting users or devices access, it checks their identities and security status.
In this day and age, NAC is significant. Cyberattacks are getting smarter as more devices are connected to networks. In this way, having major areas of strength for a framework is significant for associations.
Here are the critical things to remember while setting up a NAC framework:
- Your Organization’s Needs:
The NAC framework ought to be customized to what your Organization needs. This includes the types of devices and users you have, how secure you need to be, and what you can afford.
- Using Up-to-date Technology:
Since NAC systems are always evolving, select one that employs the most recent technology to protect against the most recent threats.
- Scalability:
Your business should expand along with the NAC system. The NAC system ought to expand in tandem with your organization.
- Cost:
NAC systems can be expensive, so make sure you can afford them.
Your company’s safety relies heavily on NAC systems. They contribute to the prevention of numerous threats to networks.
Here are some additional memorable things while setting up an NAC framework:
- Associate the NAC framework with other security frameworks like firewalls and interruption indicators for better security.
- Ensure the NAC framework is not difficult to utilize and keep up with to keep it working accurately.
- Keep the NAC framework refreshed to remain protected from new dangers.
- Organizations can choose an NAC system that protects their networks from today’s threats by carefully considering these factors.
